
On August 5th, 2025, KuCoin released its latest Security Weekly Channel, which highlighted a sobering reality for the Web3 ecosystem. According to the report, which drew on data from blockchain security firm SlowMist, security incidents in July 2025 drained approximately $147 million in total losses. These figures are more than just a grim tally; they serve as a stark reminder that risk is not an anomaly in the crypto world. It is an inherent and multifaceted reality that affects every participant, from developers to the average user.
A closer look at the month's major hacks reveals three distinct categories of risk that collectively define Web3's security challenges.
Smart Contracts: The Double-Edged Sword of Web3
For many, the promise of Web3 lies in its reliance on immutable code. But as July's incidents show, a single logical error can be catastrophic. The decentralized trading platform GMX was hit for over $42 million after attackers exploited a subtle vulnerability in its Keeper system's logic. By manipulating how the protocol handled short positions and price updates, the hackers managed to inflate the price of GLP, allowing them to profit from a massive redemption.
Similarly, the ZKSwap cross-chain bridge hack, which resulted in a $5 million loss, stemmed from a fundamental flaw. The zero-knowledge proof mechanism—a core security feature—was not actually being verified, allowing an attacker to forge withdrawal proofs and bypass the system's most crucial security check. The case of the SuperRare smart contract, which had a low-level error where != was used instead of ==, further underscores this point. [2] These attacks highlight a critical truth: in a system built on code, even a minor mistake can create a major security hole.
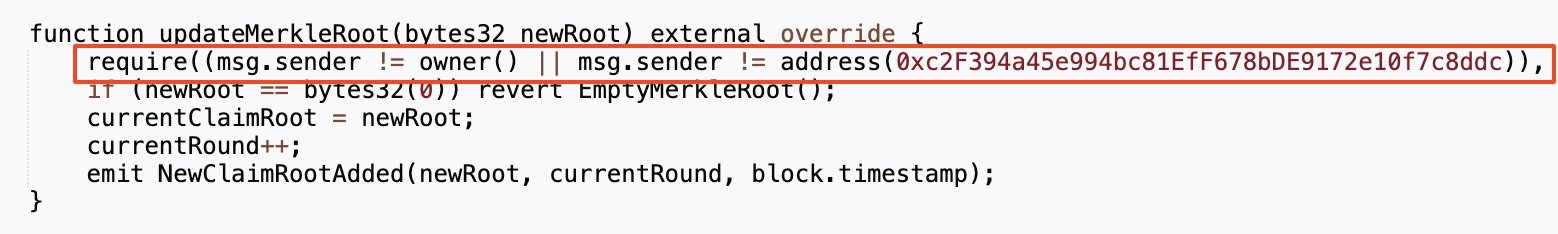
Credit: @SlowMist_Team on X (Twitter)
From Insiders to Keyloggers: The Web3 Attack Surface Widens
While code is often the primary focus, July's most alarming trend was the increasing sophistication of attacks targeting the people behind the platforms. This is where the vulnerabilities of centralized systems truly come to light. The CoinDCX hack, which cost $44.2 million, was not a direct assault on its wallets but an inside job facilitated by a compromised software engineer. Attackers posed as freelance recruiters, installed a keylogger on the employee's computer, stole his login credentials, and gained access to the exchange’s internal systems. The subsequent arrest of the engineer demonstrates the severe consequences of such a breach, and the incident exposes how social engineering remains a highly effective attack vector. [1]
Another example, the BigONE supply chain attack, saw hackers infiltrate the exchange’s production network and alter the operating logic of its risk control systems, resulting in a $27 million loss. The WOO X hack, which drained $14 millionfrom nine user accounts, was also tied to a targeted phishing attack on a team member. These incidents highlight that no matter how secure an exchange's cold storage is, its internal infrastructure—and the employees who manage it—present a significant attack surface that bad actors are increasingly keen to exploit.
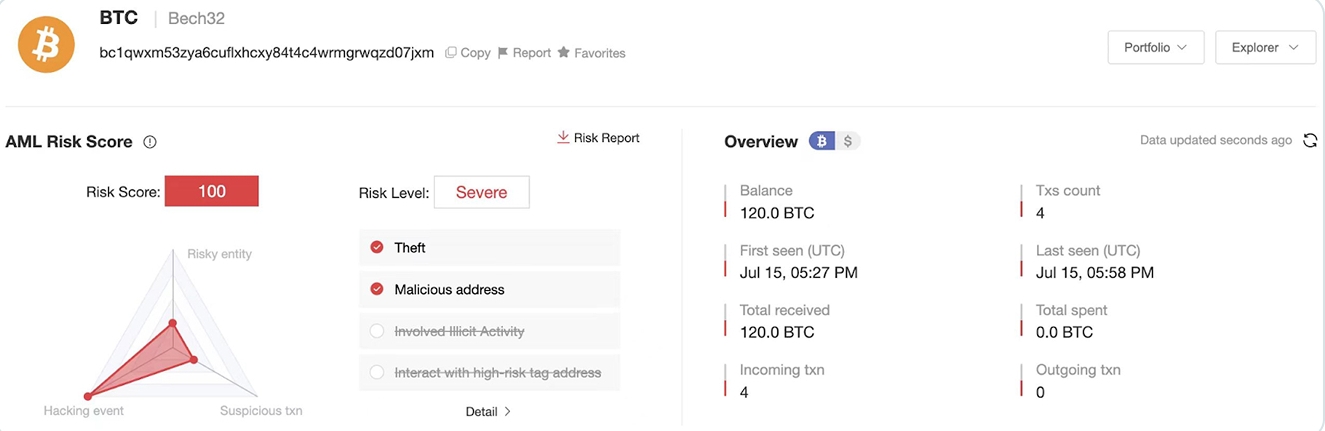
Credit: @SlowMist_Team on X (Twitter)
User-Driven Risk: The Last Line of Defense
Perhaps the most tragic losses are those resulting from a lack of user education and awareness. The report includes a harrowing story of a user who lost 4.35 BTC—a significant sum—after purchasing a counterfeit cold wallet from a third-party seller on an e-commerce platform [3]. The pre-configured device was a trap, designed to siphon funds as soon as they were transferred. This story serves as a powerful reminder that security is not just the responsibility of platforms and protocols.
For the average user, the risks of Web3 are unique. They are not protected by bank-level insurance or traditional fraud departments. The decentralized nature of the technology places a heavy burden of responsibility on the individual, making due diligence in everything—from purchasing hardware wallets to validating transaction details—absolutely paramount.
Conclusion: A Shared Responsibility
The security events of July 2025, as detailed in KuCoin's report, serve as a powerful summary of Web3's inherent risks. They demonstrate that the ecosystem is being simultaneously tested by technical flaws in smart contracts, human-driven attacks on centralized entities, and a persistent lack of user awareness. The $147 million in losses is a wake-up call for the entire industry. It's a clear signal that security can no longer be seen as an afterthought. Instead, it must be an integrated, collaborative effort involving robust technical audits, stringent internal protocols, and a widespread commitment to user education. Only by addressing all three fronts can the industry hope to build a truly secure and resilient digital future.

References
[1] FinanceFeeds - CoinDCX Software Engineer Arrested in $44 Million Insider-Aided Crypto Heist, July 31, 2025
[2] X(Twitter) - SlowMist TI Alert, July 28, 2025 (https://x.com/SlowMist_Team/status/1949770231733530682)
[3] X(Twitter) - A User's Hacking Experience of Purchasing Cold Wallet through Unofficial Channels, July 29, 2025 (https://x.com/0xdizai/status/1949906538497528087)











