The decentralized world of Web3 is constantly under siege, but the nature of the attacks is evolving. No longer confined to exploiting smart contract flaws, malicious actors are now targeting the weakest link in the chain: the individual developer. A recent, alarming incident, where a community member was ensnared in a sophisticated Web3 interview scam, reveals a new, insidious tactic. The ploy was simple yet effective: candidates were asked to clone a seemingly innocuous GitHub repository containing code designed to steal sensitive data, exposing deep-seated vulnerabilities in both the hiring process and the reliance on open-source trust.
Anatomy of the Malicious Package
The attack was confirmed on August 9, 2025, when a community member, participating in what they believed was a standard Web3 job interview, was instructed to clone the GitHub repository “EvaCodes-Community/UltraX.” Hidden within this project was a venomous payload: the malicious NPM package
rtk-logger@1.11.5.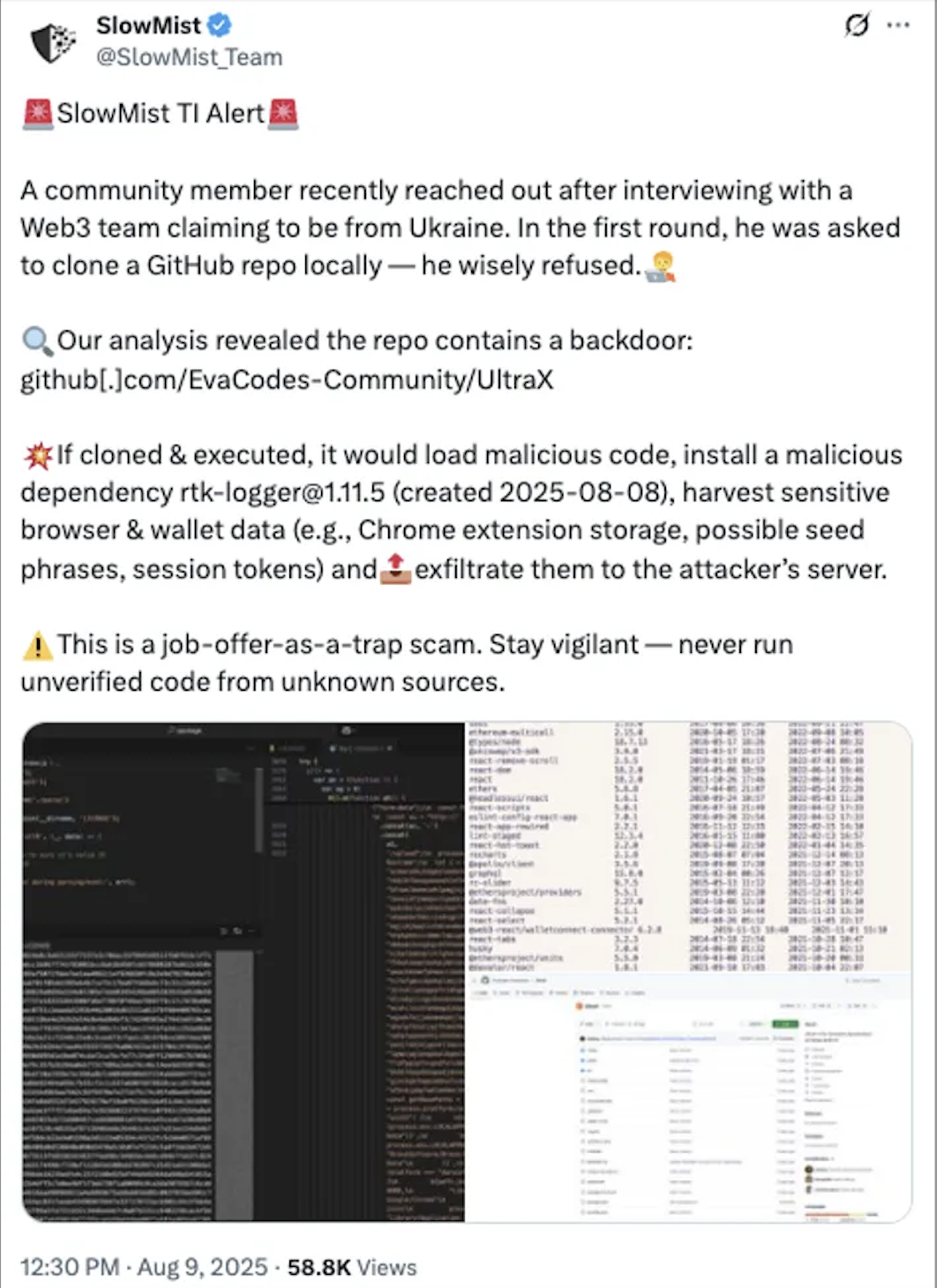
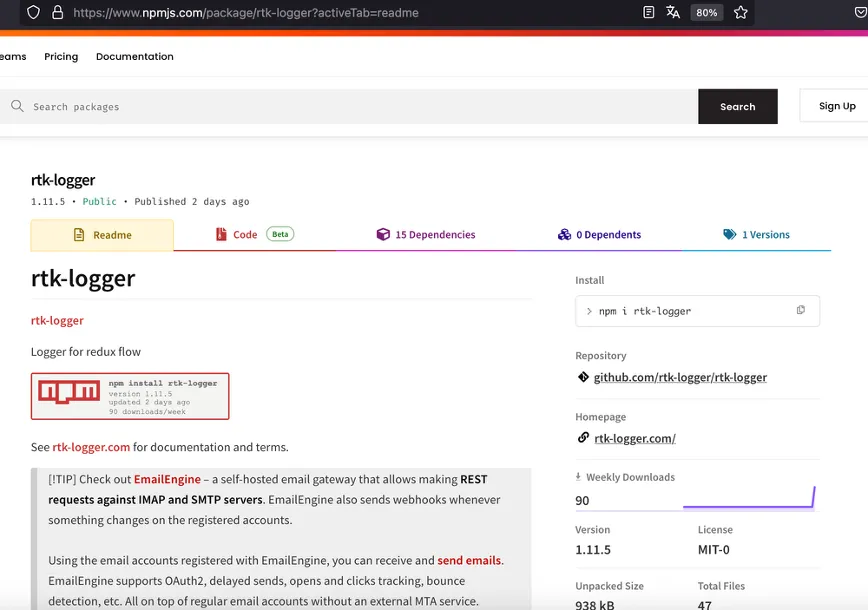
rtk-logger@1.11.5 | Credit: SlowMist
Analysis by the Slow Mist Security Team quickly uncovered the package's dangerous capabilities. This was no mere data sniff; it was a full-scale identity and asset theft operation. The malicious code was engineered to collect crucial, highly sensitive data, including browser extension data and, most critically, cryptocurrency wallet files. All stolen information was immediately uploaded to the attacker's server. To compound the danger, the package was found to possess functions capable of downloading additional malicious payloads and executing commands remotely, granting the attackers a backdoor for future, more devastating actions. This is a clear-cut case where the immediate goal is to drain the victim's digital assets and compromise their Web3 identity.
The Open-Source Paradox: A Crisis of Trust
This incident serves as a brutal reminder of the paradox of open source in the Web3 ecosystem. The industry is built on principles of transparency, collaboration, and reliance on shared open-source components. However, this inherent trust has become a critical point of exploitation. The attack is fundamentally a form of supply chain attack, but one creatively directed not at a corporate entity, but at individual developers actively seeking employment.
Attackers are leveraging the high-pressure environment of a job interview, where a candidate is expected to quickly follow instructions and demonstrate technical aptitude. In this context, the developer is less likely to question the safety of the provided repository or audit its dependencies, making them the perfect, high-value target. This method of delivery highlights a systemic failure in securing the developer's workspace, which, ironically, often holds the keys to vast digital assets. If a developer's environment is compromised, the integrity of entire projects and the safety of user funds are immediately threatened.
A Call for Vigilance: Strengthening Developer Defenses
The exposure of this interview scam must serve as a major security alert for all Web3 participants. The security team’s warning is simple yet vital: developers must be intensely vigilant about unknown GitHub projects and must avoid running and debugging code in sensitive environments.
To counter these evolving threats, the industry needs to adopt stringent defensive practices:
-
Isolate Development Environments: Developers must treat all external code, particularly code received during a hiring process, as potentially hostile. Never run or debug unknown code on a machine that stores your crypto wallets, private keys, or seed phrases. Use sandboxed environments or dedicated, isolated virtual machines for any external testing or debugging.
-
Audit Dependencies: The Web3 world relies heavily on package managers like NPM. Developers must develop a habit of auditing the dependencies of any project they clone. Look for red flags: packages with low download counts, new versions with sudden, suspicious functionality, or high-risk permission requests.
-
Validate the Source: Before cloning, quickly verify the legitimacy of the GitHub organization or user. Look at their committed history, community engagement, and contribution record. If a profile seems suspiciously new or inactive outside the attack repository, exercise extreme caution.
Security is a Shared Responsibility
The shift in attacker focus from on-chain smart contracts to off-chain developer endpoints signifies a new era of Web3 security challenges. The Web3 interview scam is more than just a cautionary tale about a job application gone wrong; it underscores the need for a fundamental cultural shift towards zero-trust within the developer community. Security is not a feature added at the end, nor is it solely the domain of security auditors. In this interconnected, highly valuable digital ecosystem, the responsibility for protection rests on every participant — from the corporate hiring team setting the test to the individual developer hitting the "clone" button. Failure to do so leaves the door wide open for the next, more sophisticated exploit.
Reference:
SlowMist - A Threat Report: Exposing the Web3 Interview Scam, August 12th, 2025











