The digital landscape of Web3 is a frontier of both immense innovation and high-stakes risk. The recent liquidity vulnerability attack on Odin.fun, a Bitcoin-based memecoin platform, serves as a stark reminder of this reality. The attack resulted in the loss of 58.2 bitcoins, valued at roughly $7 million. While the financial damage was significant, the platform’s swift and transparent response, spearheaded by co-founder Bob Bodily, is now being hailed as a critical case study in crisis management, showing how centralized action and open communication can be vital for a decentralized ecosystem's survival.
The Attack and the Path to Recovery
The attack, which exploited a liquidity vulnerability, blindsided the platform. In the aftermath, the Odin.fun team moved quickly to not only contain the damage but also to actively pursue the stolen funds. As Bob Bodily announced on August 19, the team has successfully frozen a portion of the hackers' funds across various Centralized Exchanges (CEXs)and in associated tokens. This crucial step highlights the often-overlooked role of centralized entities in the recovery of stolen assets within the ostensibly decentralized Web3 world.
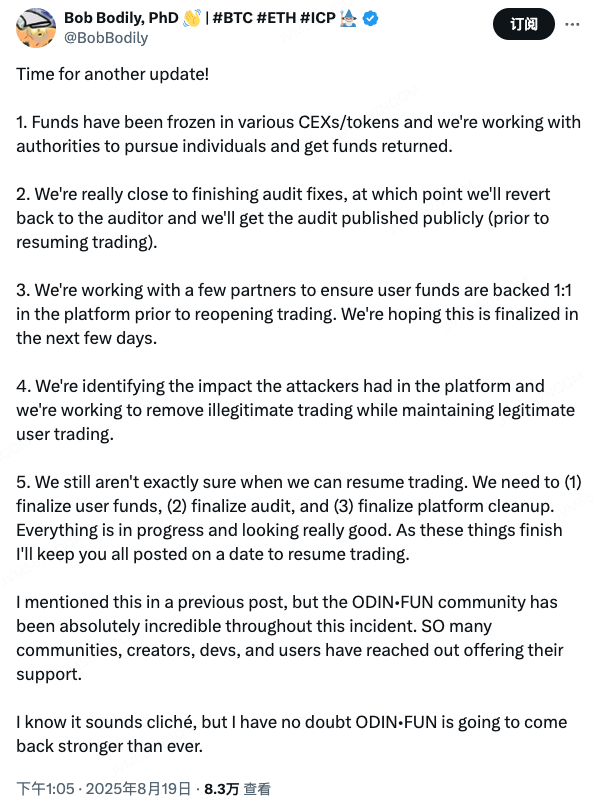
Beyond asset recovery, the team is also working closely with authorities to track down the perpetrators. On the technical front, they are nearing the completion of a thorough audit and repair of the platform's smart contracts. Bodily promised that once the audit firm completes its review, a public report will be released, providing full transparency into the vulnerability and its fix. This commitment to public disclosure is a powerful tool for rebuilding trust.
A Tale of Two Systems: Centralization Meets Decentralization
The Odin.fun incident is a textbook example of the enduring paradox in today's Web3 space. While the protocol itself operates on a decentralized blockchain, the recovery process is heavily reliant on centralized choke points. Centralized Exchanges (CEXs) became a critical line of defense, acting as a barrier to the hackers' ability to cash out. Without the ability to freeze funds on these platforms, asset recovery would be an almost impossible task.
Furthermore, the response highlights the immense power of transparency. In a decentralized community where trust is paramount, the lack of a central authority means that open communication becomes the most effective tool for managing a crisis. By providing regular updates on social media, Bodily didn’t just inform the community; he managed their expectations and demonstrated accountability. This proactive approach helps to quell panic and maintain confidence, a sharp contrast to projects that go silent after a security breach, often leading to a complete loss of user trust.
The promise to publish the audit report is another key pillar of this strategy. A successful attack on a protocol's code is a major blow to its credibility. A public audit report not only confirms that the vulnerability has been patched but also demonstrates that the team has learned from its mistakes and is committed to long-term security. This is the foundation upon which trust can be rebuilt.
A Blueprint for the Future
Odin.fun’s response should be seen as a new standard for crisis management in the Web3 space. While the attack itself underscores the ever-present risks for new and innovative protocols, the team's professional and decisive actions offer a positive precedent. They have shown that a swift response, leveraging both centralized cooperation and transparent communication, is a powerful recipe for navigating a security crisis.
For the broader Web3 industry, this event serves as a crucial lesson. Projects must not only prioritize robust code audits from day one but also establish clear and effective crisis communication plans. It is no longer enough to build a secure protocol; teams must also prepare for the inevitable—an attack on their system. The ability to recover, restore confidence, and leverage every available tool, both centralized and decentralized, will define which projects succeed and which ones fade away after a security breach.











