The world of cryptocurrency, for all its revolutionary promise, remains a volatile frontier. A recent security report from KuCoin highlights this reality, bringing to light a series of vulnerabilities that have rattled the industry. Among the most alarming incidents detailed is a suspected "51% attack" on Monero (XMR), a privacy-centric cryptocurrency. This event, currently unfolding amid community dispute and speculation, serves as a stark reminder of the inherent risks lurking beneath the surface of seemingly robust decentralized networks.
The Unfolding Monero Incident
On August 12th, @CaffeinatedUser reported that suggesting that Monero was in the throes of a successful 51% attack on X(Twitter).
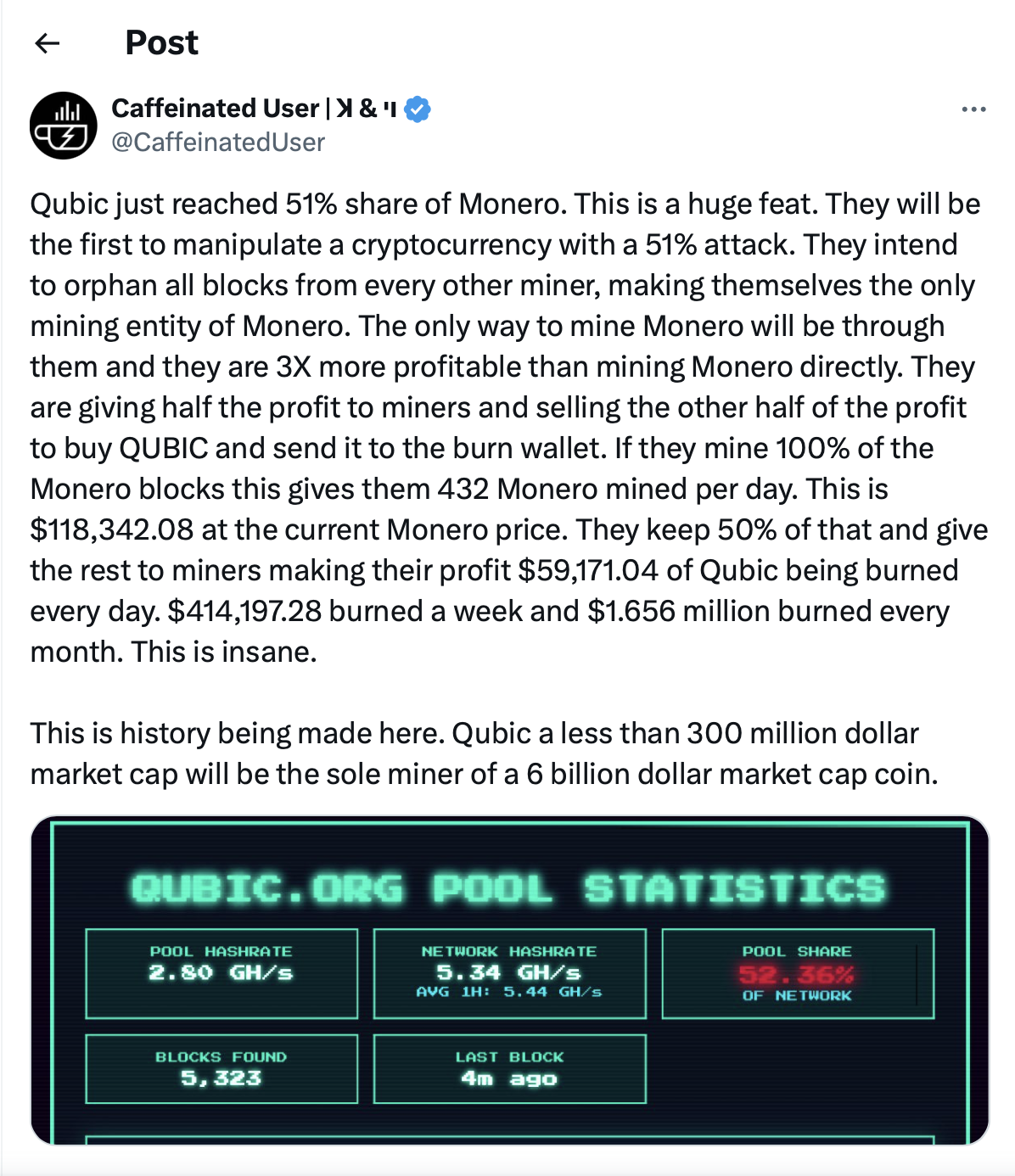
The alleged perpetrator is the Qubic mining pool, which brazenly claimed to have amassed over 51% of Monero’s network hash rate. This claim, however, has been met with skepticism within the crypto community, with some users suggesting that Qubic's actual hash rate is closer to 33%. While the exact figures remain unconfirmed and hotly debated, the actions taken by Qubic leave little room for doubt about their intentions.
According to KuCoin's report and a reference from a user on X, Qubic has already managed to successfully reorganize six Monero blocks. This technical maneuver is a hallmark of a 51% attack, as it allows the attacker to rewrite transaction history, potentially enabling double-spending—a fraudulent act where the same funds are spent more than once. The ability to reorganize blocks also grants the attacker the power to engage in transaction censorship, effectively blocking or delaying certain transactions from being confirmed on the network. The situation remains fluid, and relevant platforms, including exchanges, are being urged to monitor the network closely to prevent any further malicious activity.
Unpacking the 51% Attack: A Fundamental Threat to PoW
The Monero incident provides a crucial case study in the dangers of a 51% attack. At its core, this attack exploits the fundamental mechanics of a Proof-of-Work (PoW) consensus mechanism. In a PoW network like Bitcoin or Monero, miners compete to solve complex cryptographic puzzles to add new blocks of transactions to the blockchain. The first one to solve the puzzle earns the right to create the new block and receives a block reward. This process is what secures the network and ensures its integrity.
A 51% attack occurs when a single entity or a coordinated group gains control of more than half of the network's total computing power, or hash rate. With this majority control, they can effectively outpace all other honest miners, giving them the power to monopolize the block creation process. This level of dominance allows them to not only reorganize recent blocks and engage in double-spending but also to censor transactions and even prevent others from mining.
What makes the Monero case particularly troubling is that it targets a network renowned for its privacy features. While Monero’s focus on privacy has made it a favorite among users seeking anonymity, its underlying PoW mechanism is not immune to centralization. The ease with which a single mining pool could potentially gain such significant control highlights a vulnerability that every PoW-based cryptocurrency must contend with. The promise of decentralization, the very bedrock of crypto, is called into question when a single actor can wield such disproportionate power.
The Crypto Exchange: The Role of Centralized Gatekeepers
The crypto exchange, as a centralized entity, acts as a crucial gatekeeper in the crypto ecosystem. When a network like Monero faces a potential attack, exchanges bear a significant responsibility to protect their users. This includes implementing robust monitoring systems, pausing withdrawals or deposits of the affected token, and being ready to halt trading if necessary. The Monero attack underscores the paradoxical but necessary role of centralized platforms in a decentralized world: they serve as a critical line of defense against on-chain vulnerabilities.
The incident also reignites the long-standing debate about the delicate balance between decentralization and security. While cryptocurrencies were designed to eliminate the need for central authorities, the reality is that the concentration of mining power in a handful of large pools creates a de facto centralization. This poses a systemic risk, and projects must constantly innovate to prevent such concentrations. The Monero community’s internal dispute over the attacker's true hash rate further emphasizes the lack of transparency in the mining landscape, making it difficult for users and platforms alike to accurately assess risk in real-time.
Conclusion: A Wake-Up Call for the Crypto Community
The suspected 51% attack on Monero serves as a powerful wake-up call. It's a reminder that even the most established and privacy-focused cryptocurrencies are not invincible. The ease with which a mining pool could allegedly attempt to manipulate the network highlights the ongoing challenges of securing decentralized systems. As the crypto industry matures, it must address these foundational vulnerabilities head-on. This requires not only technological innovation but also greater transparency within mining communities and a proactive stance from exchanges and other key players. The integrity of the entire ecosystem depends on a collaborative effort to fortify its defenses against a threat that is no longer theoretical but demonstrably real.











